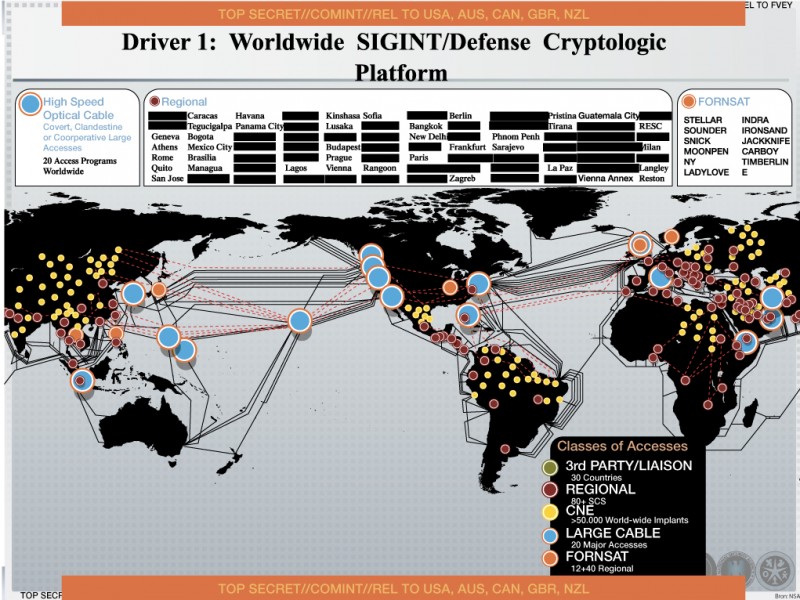
A new map leaked by former NSA-employee Edward Snowden shows how the National Security Agency used malicious software to infiltrate more than 50,000 computer networks around the world. According to the dutch newspaper NRC the malware was used to steal sensitive information.
NRC got hands on a management presentation dating from 2012 that explains how the NSA collects information worldwide. It shows that the agency uses „Computer Network Exploitation“ (CNE) in more than 50,000 locations around the globe. These activities are carried out by a team of about 1000 elite hackers, called Tailored Access Operations team (TAO).The US newspaper Washington Post previously documented how the TAO team works. By exploiting weaknessess around the world, the NSA hackers were able to install their malware in many networks and build yet another surveillance network.
A yellow dot on the map signifies a CNE infection. Once the malware is installed, the NSA can flip it on or off any time. By infecting the network, the NSA gains unfiltered access to it’s information.
As NRC reports, the British intelligence service GCHQ uses this method as well. The Dutch newspaper writes that the belgian telefom provider Belgacom discovered this type of hacking into its system in September 2013. The malware installed by the GCHQ was used to tap Belgacom’s customer’s telephone and data traffic. The malware infiltrated the system by luring Belgacom employees to visit a false LinkedIn page.
The map also shows that the majority of CNE operations is carried out in Europe, South America and Asia. It seems possible that the CNE operations focus on Internet service providers, telecom giants and other similar companies aiming to facilitate massive information collection.
When NRC confronted NSA and the US Government with the newest revelations, they declined to comment.
erschienen auf netwars-project.com
Schreibe einen Kommentar
Du musst angemeldet sein, um einen Kommentar abzugeben.